
Directory services are becoming a key part in managing IT infrastructure. Microsoft's service, Active Directory (AD), is one of the most well-known directory services in the world. In this article, we will cover the basics and explain exactly what Active Directory is and how to use it.
Network Security and Administration ExpertUpdated: December 29, 2023

The increasing intricacy of networking resources has elevated the significance of directory services in managing IT infrastructure.
Among these services, Active Directory stands out as a prominent name. This directory service from Microsoft has become a fundamental tool for network administrators.
In this Active Directory tutorial we’re going to look at what Active Directory is, how to use it, and Active Directory tools like ManageEngine AD360 and SolarWinds Access Rights Manager.
Topics include:
Active Directory is a directory service or container which stores data objects on your local network environment. The service records data on users, devices, applications, groups, and devices in a hierarchical structure.
The structure of the data makes it possible to find the details of resources connected to the network from one location. In essence, Active Directory acts like a phonebook for your network so you can look up and manage devices easily.
There are many reasons why enterprises use directory services like Active Directory. The main reason is convenience. Active Directory enables users to log on to and manage a variety of resources from one location. Login credentials are unified so that it is easier to manage multiple devices without having to enter account details to access each individual machine.
Other leading reasons include enhanced security and simplified administration. Active Directory provides robust security features, such as centralized policy management and access control, which helps in safeguarding sensitive data. Additionally, it streamlines administrative tasks by allowing network administrators to easily create and manage user accounts, set permissions, and deploy software across the network. Its scalability is another advantage, making it suitable for organizations of all sizes.
Network administrators turn to AD for these main strengths:
To begin you will need to first make sure that you have Windows Professional or Windows Enterprise installed otherwise you won’t be able to install Remote Server Administration Tools. Then do the following:
For Windows 10 Version 1809 and Windows 11:
For Windows 8 (And Windows 10 Version 1803)
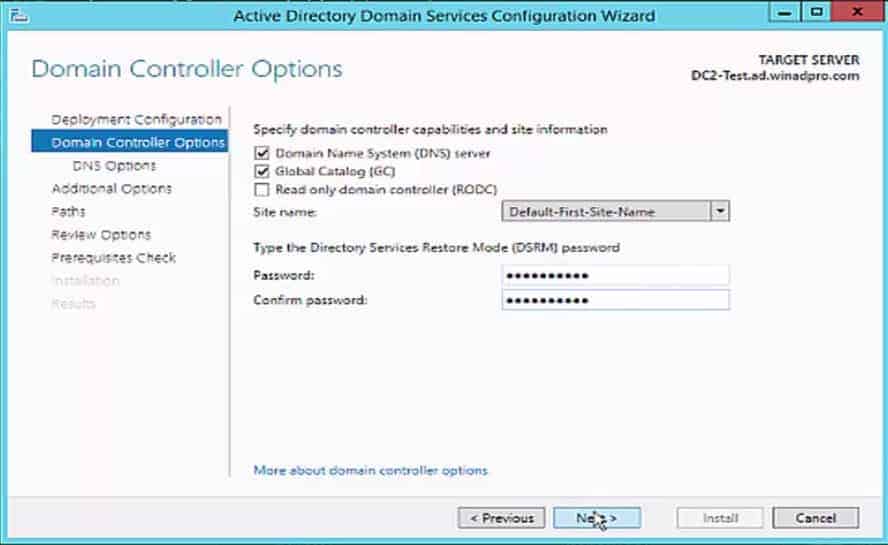
One of the first things you need to do when using Active Directory is to set up a domain controller. A domain controller is a central computer that will respond to authentication requests and authenticate other computers throughout the network. The domain controller stores the login credentials of all other computers and printers.
All other computers connect to the domain controller so that the user can authenticate every device from one location. The advantage of this is that the administrator won’t have to manage dozens of login credentials.
The process of setting up a domain controller is relatively simple. Assign a static IP address to your Domain Controller and install Active Directory Domain Services or ADDS. Now follow these instructions:
The procedures for adding a domain controller to an existing domain in Active Directory are the same, no matter which operating system you have. However, these instructions were organized during an exercise on Windows Server 2016. It is always a good idea to have at least two domain controllers in your AD domain just in case one goes down.
The second Domain Controller is a separate computer from the one identified for your first Domain Controller. That second computer needs to be set up with Windows Server 2016. Get it fully patched and assign it an IP address before starting the AD setup on that machine. Then follow these steps:
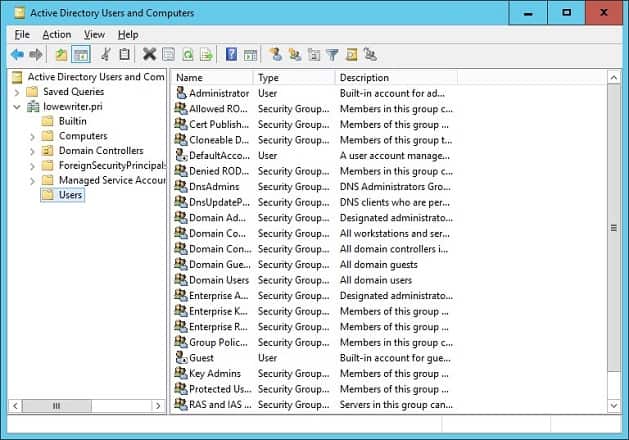
Go back to your original domain controller computer and open Active Directory Users and Computers and you will see that your new DC is listed there in the Domain Controllers folder.
Users and computers are the two most basic objects that you will need to manage when using Active Directory. In this section, we’re going to look at how to create new user accounts. The process is relatively simple, and the easiest way to manage users is through the Active Directory Users and Computer or ADUC tool that comes with the Remote Server Administration Tools or RSAT pack. You can install ADUC by following the instructions listed below:
Install ADUC on Windows 10 Version 1809 and Higher or Windows 11:
Install ADUC on Windows 8 and Windows 10 Version 1803 or Lower:
How to Create New Users with ADUC
Like all forms of infrastructure, Active Directory needs to be monitored to stay protected. Monitoring the directory service is essential for preventing cyber-attacks and delivering the best end-user experience to your users.
Below we’re going to list some of the most important network events that you should look out for. If you see any of these events then you should investigate further ASAP to make sure that your service hasn’t been compromised.
| Current Windows Event ID | Legacy Windows Event ID | Description |
|---|---|---|
| 4618 | N/A | A security event pattern has been recognized. |
| 4649 | N/A | A replay attack was detected (potentially a false positive). |
| 4719 | 612 | A system audit policy was changed. |
| 4765 | N/A | SID History added to an account. |
| 4766 | N/A | The attempt failed to add SID History to account. |
| 4794 | N/A | Attempt to launch Directory Services Restore Mode. |
| 4897 | 801 | Role separation enabled. |
| 4964 | N/A | Special groups have been assigned a new logon. |
| 5124 | N/A | Security updated on OCSP Responder Service. |
| N/A | 550 | Potential DoS attack. |
| 1102 | 517 | Audit log was cleared. |
Forest and trees are two terms you will hear a lot when delving into Active Directory. These terms refer to the logical structure of Active Directory. Briefly, a tree is an entity with a single domain or group of objects that is followed by child domains. A forest is a group of domains put together. When multiple trees are grouped together they become a forest.
Trees in the forest connect to each other through a trust relationship, which enables different domains to share information. All domains will trust each other automatically so you can access them with the same account info you used on the root domain.
Each forest uses one unified database. Logically, the forest sits at the highest level of the hierarchy and the tree is located at the bottom. One of the challenges that network administrators have when working with Active Directory is managing forests and keeping the directory secure.
For example, a network administrator will be tasked with choosing between a single forest design or multi-forest design. The single-forest design is simple, low-cost and easy to manage with only one forest comprising the entire network. In contrast, a multi-forest design divides the network into different forests which is good for security but makes administration more complicated.
The easiest way to find account lockouts in Active Directory is to use the Event Viewer, which is built into Windows. Active Directory generates Windows Events messages for each of its actions, so your first task is to track down the right event log.
The Event Report will show you the user that was locked out, the computer that the event occurred on, and the source, or reason for the lockout.
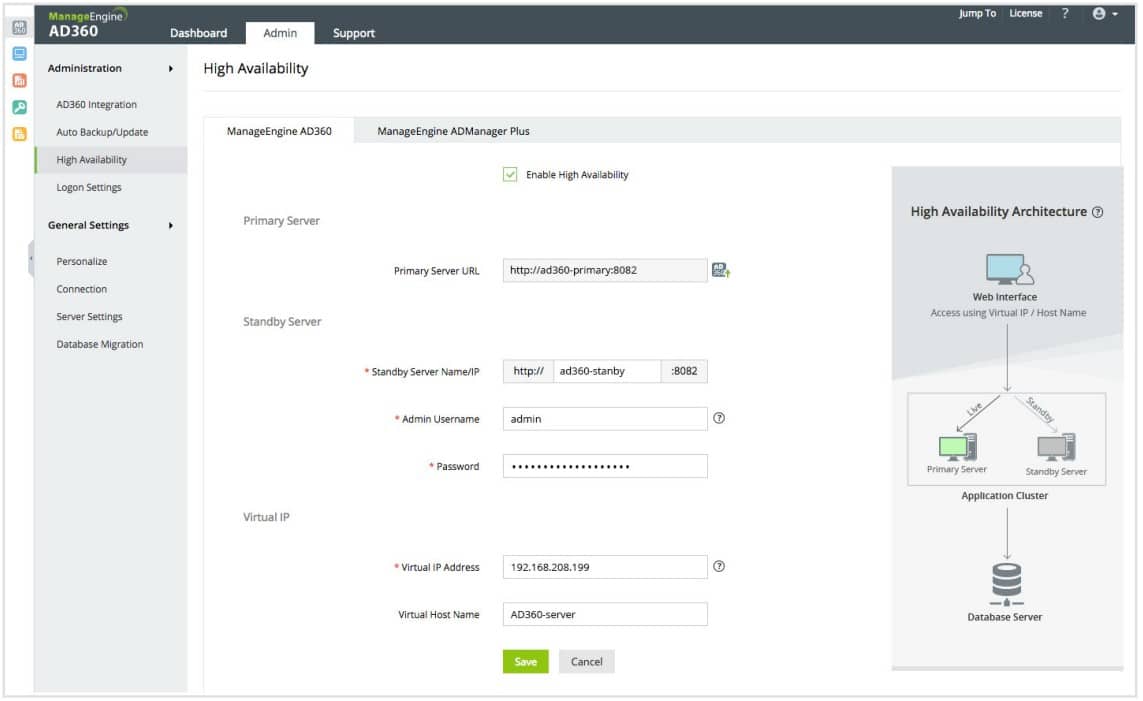
ManageEngine AD360 is a compendium of ManageEngine Active Directory management systems plus a backup and recovery service. This package represents a good example of the tools that are available to automate the management tasks surrounding Active Directory usage. It is able to interface to AD implementations for SharePoint, Microsoft 365, Azure, and AWS, as well as the Active Directory system that you have in your Windows Server operating system.
ManageEngine AD360 is available on a 30-day free trial.
As mentioned above, trusts are used to facilitate communication between domains. Trusts enable authentication and access to resources between two entities. Trusts can be one-way or two-way in nature. Within a trust, the two domains are divided into a trusting domain and a trusted domain.
In a one-way trust, the trusting domain accesses the authentication details of the trusted domain so that the user can access resources from the other domain. In a two-way trust, both domains will accept the other’s authentication details. All domains within a forest trust each other automatically, but you can also set up trusts between domains in different forests to transfer information.
You can create trusts through the New Trusts Wizard. The New Trust Wizard is a configuration wizard that allows you to create new trust relationships. Here you can view the Domain Name, Trust Type, and Transitive status of existing trusts and select the type of trust you want to create.
There is a range of trust types in Active Directory. We’ve listed these in the table below:
| Trust Type | Transit Type | Direction | Default? | Description |
|---|---|---|---|---|
| Parent and child | Transitive | Two-way | Yes | A parent and child trust is established when a child domain is added to a domain tree. |
| Tree-root | Transitive | Two-way | Yes | A tree-root trust is established the moment a domain tree is created within a forest. |
| External | Non-transitive | One-way or two-way | No | Provides access to resources in a Windows NT 4.0 domain or a domain located in a different forest that isn’t supported by a forest trust. |
| Realm | Transitive or non-transitive | One-way or two-way | No | Forms a trust relationship between a non-Windows Kerberos realm and a Windows Server 2003 domain. |
| Forest | Transitive | One-way or two-way | No | Shares resources between forests. |
| Shortcut | Transitive | One-way or two-way | No | Reduces user logon times between two domains within a Windows Server 2003 forest. |
Generating reports on Active Directory is essential for optimizing performance and staying in accordance with regulatory compliance. One of the best Active Directory reporting tools is SolarWinds Access Rights Manager (ARM). The tool has been created to increase visibility into how directory credentials are used and managed. For example, you can view accounts with insecure configurations and credential abuse that could indicate a cyber attack.
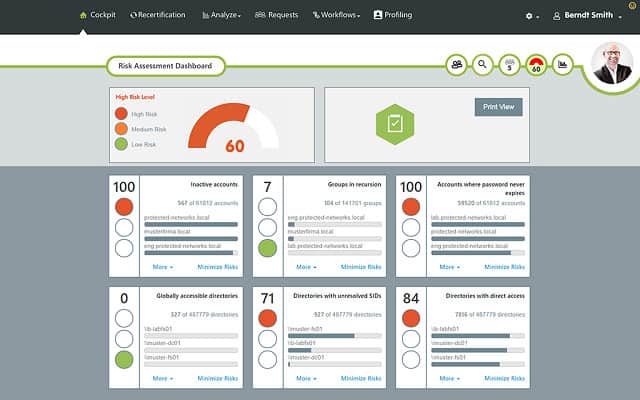
Using a third-party tool like SolarWinds Access Rights Manager is beneficial because it provides you with information and features that would be much more difficult or impossible to access through Active Directory directly.
As well as generating reports you can automatically delete inactive or expired accounts that cybercriminals target. SolarWinds Access Rights Manager starts at $3,444 (£2,829). There is also a 30-day free trial version that you can download.
Active Directory is one of the best tools for managing resources in your network. In this article, we’ve just scratched the surface of the potential of this tool. If you’re using Active Directory remember that it is a potential entry point for cyber attackers. Making a note of key directory events and use a directory monitor will go a long way towards minimizing the risk of a malicious attack and protecting the availability of your service.
Active Directory is an authentication system. A domain is a collection of objects, which are users, computers, and devices that all have access rights managed in the same Active Directory database. The domain controller is the authentication management system that implements Active Directory functions on the domain’s database objects.
In order to start security auditing within Active Directory:
The Lightweight Directory Access Protocol (LDAP) is an open standard that outlines how access rights can be managed. Active Directory is an access rights management system, written by Microsoft. Active Directory is an evolution of the concepts defined in LDAP.
Single sign-on (SSO) gives each user access to several systems with just one authentication procedure. Active Directory (AD) is an access rights management system that can implement an SSO environment.
No. Active Directory is a server function and it is integrated into the Windows Server operating system. Logically, any client running Active Directory would become a server.
We reviewed the market for Active Directory monitoring software and analyzed the options based on the following criteria: